There’s so much “cybersecurity SEO” content floating around the internet that you have to wonder: is this actually specialized knowledge, or just regular SEO with a fancy trench coat and fake mustache? I’ll let you be the judge, but here at The OAG, cybersecurity SEO isn’t just something we dabble in while waiting for our real careers to take off. It’s our whole deal.
The cybersecurity sector demands specific attention and coverage by those who understand the niche. It is fellow experts, fellow analysts, fellow PKI administrators, sys admins, and CISOs who are asking the questions leading to your security offerings. Without cybersecurity-specific SEO optimization, their highly specified brand of traffic is going to pass your company by.
What’s more, search engines have evolved to understand context and user intent with frightening accuracy. That means generic “one-size-fits-all” SEO approaches simply won’t cut it in specialized fields like cybersecurity.
Search engines now recognize when content truly addresses the technical depth that security professionals demand versus content that’s just throwing around buzzwords. This sophistication means cybersecurity companies need sophisticated SEO that speaks the language of both algorithms and security pros.
Our experience working in the cybersecurity industry has taught us that SEO isn’t just about driving traffic—it’s about establishing trust in a high-stakes industry.
Here’s how to really optimize for cybersecurity SEO – and stay in the running for Google’s Page One.
11 Hot Tips for Optimizing Cybersecurity SEO
Let’s dive right in. Here are 11 tips you can use to improve your cybersecurity SEO in ways that truly move the needle. Or, if you don’t have time to do it yourself, things that your SEO consultants should be doing for you.
- Security Credential Highlighting: Feature cybersecurity certifications (CISSP, CEH, CISM) prominently in your content and schema markup to build trust. Don’t be afraid to flash those authority signals; you’ve earned them, and interested customers want to see them. By highlighting the talent among your team, you make your organization a serious industry contender. Being able to verify these credentials with embedded LinkedIn links will only bolster your credibility.
- Threat Intelligence Keywords: Create content around emerging threats and vulnerabilities using specific CVE numbers and threat actor names that cybersecurity professionals actively search for. General security blogs have their place, especially in the SEO pantheon, but once cybersecurity experts identify your site as a watering hole with real information based on specific threats, you’ll be a place they frequent time and again.
- Technical Documentation Optimization: Optimize technical security documentation with highly specific long-tail keywords that security professionals use when troubleshooting (e.g., “mitigating log4j vulnerability in legacy systems”). This will take interested administrators directly to your site. This familiarity with your organization and the value you bring will come to bear when future solutions conversations come up. Building your brand as an authority that can speak the language of cybersecurity professionals is the first step to getting a foot in the door.
- Trust-Signal Rich Snippets: Add specialized schema markup to showcase your security badges, compliance certifications, and guarantees directly in search results. With AI-generated content and online scams on the rise, consumers are cautious. Research shows that 70% of people trust third-party verification, while less than half believe claims made by websites themselves. Those external badges and certifications serve an important purpose — prospects look for validation, and seeing your brand referenced on reputable industry sites strengthens your authority.
- Calculator Tools: Develop interactive calculators that help organizations understand the financial implications of ransomware attacks, attracting high-intent traffic. This is a great strategy for attracting non-technical decision-makers like CEOs and companies still in the research phase of their cybersecurity buyer’s journey.
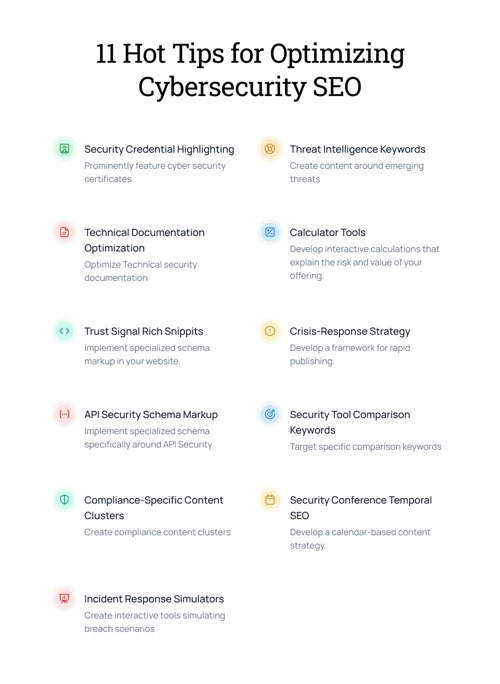
- Crisis-Response Content Strategy: Create a system for quickly publishing authoritative content when major security breaches happen, targeting terms people frantically Google during security incidents. It’s called news jacking, and timing is everything. During a crisis, companies desperately need trusted voices to tell them whether to panic or not. If your team can publish thoughtful analysis when high-profile cybersecurity disasters strike, you’ll not only capture that urgent traffic spike but position yourself as the go-to expert for future meltdowns.
- API Security Schema Markup: Implement specialized schema for API security documentation that helps your content appear in developer-focused search results. APIs are now business critical, with the average small business running anywhere from 10 to 30 of them. As your organization showcases its API security offerings, it is going to show up in more and more of these circles – and searches.
- Security Tool Comparison Keywords: Target specific keywords comparing security tools and solutions that have high conversion potential (e.g., “EDR vs XDR solutions for financial institutions”). As B2B clients navigate the buyer’s journey, comparing and contrasting different solutions is always going to be a necessary pit stop. Catch potential customers at the juncture as you help them make their choice: your SEO stats will thank you for it.
- Compliance-Specific Content Clusters: Create content clusters around specific compliance standards (GDPR, HIPAA, CMMC) that your cybersecurity solutions address. Compliance is a tricky topic, and everyone from CISOs to GRC specialists wants to know more. If you can create a series of compliance-related assets, you not only provide more value but also increase time spent on your site, which in turn increases conversions.
- Security Conference Temporal SEO: Develop a calendar-based content strategy targeting major security conferences like BlackHat, DefCon, and RSA. These should be scheduled to come out before, during, and after the event to capitalize on maximum hype when search traffic spikes for specific topics.
- Incident Response Simulators: Create interactive tools that simulate breach scenarios. These generate valuable engagement signals and backlinks while demonstrating your expertise. Check out this example from Group-IB.
Know Your Target Audience (No, Really Know Them)
Let’s face it, the target audience for cybersecurity content isn’t your average internet browser looking for cat videos. We’re talking about people who can tell if you’re faking it from paragraph one. They’re skeptical by profession and can smell generic content from a mile away.
Your SEO strategies need to reflect this reality. Rather than chasing vanity metrics like total page views, focus on attracting qualified eyeballs. One CISO who stays on your site for five minutes is worth more than a hundred random visitors who bounce after ten seconds. This means crafting content that demonstrates technical credibility while still being accessible enough that it doesn’t read like an encryption algorithm.
The cybersecurity professional’s search behavior is distinctive: they use highly technical terms, they search for specific solutions to specific problems, and they value substance over style. Your content strategy should mirror this behavior pattern or you’ll be optimizing for the wrong audience entirely.
Understanding search intent is key to effective cybersecurity SEO. When someone searches “what is endpoint protection,” they’re seeking information because they’re unfamiliar with the concept – that’s informational intent.
In contrast, when they search “best endpoint protection,” they’re comparing vendors – that’s commercial intent.
This distinction matters. By mapping your content to different stages of the buyer’s journey, you ensure you’re meeting prospects where they are – whether they’re just gathering information or ready to evaluate solution providers.
Recognizing these different search behaviors helps you create content that actually answers what your audience is looking for at each step of their decision process.
Online Visibility for Cybersecurity Firms
Here’s the thing about organic traffic in the cybersecurity space – it’s not just about volume, it’s about quality. And quality traffic comes from content that genuinely solves problems.
The formula is deceptively simple:
- Identify the actual technical challenges your target audience faces
- Create content that genuinely solves those challenges
- Optimize that content for relevant search terms
- Watch as the right people find you through search
But here’s where most cybersecurity companies go wrong: they start with keywords instead of starting with solutions. They ask, “What are people searching for?” instead of “What problems can we legitimately solve?” The result is hollow content that might rank temporarily but ultimately fails to convert because it doesn’t deliver what security professionals actually need.
True organic traffic growth in cybersecurity comes from being the answer to very specific, often complex questions. When your content becomes the go-to resource for solving particular security challenges, you’ll see not just traffic growth but meaningful engagement metrics that actually matter to your bottom line.
Cybersecurity start-ups looking for website traffic
Remember, who you have implementing these tactics matters. It’s one thing to read them here on a blog – and very beneficial, too, or we wouldn’t have given you this information – but it’s another entirely to have the experience to make them sing.
That’s what sets us apart at The OAG: authentic expertise and real-world experience. We’ve been around the cybersecurity block more than a few times, and we bring that knowledge to every client project, no matter the scale. Use these 11 points to evaluate how your current cybersecurity SEO strategy measures up. Sometimes the difference between good and great isn’t what you’re doing, but who’s doing it for you.
Ready to begin? Learn how The OAG can optimize your cybersecurity SEO strategy today.